Clinical workflows and communication shouldn’t be the hardest part of organ transplant operations. We provide care teams with reliable tools to simplify clinical workflows and standardize complex care pathways.
Clinical workflow automation software for complex care teams
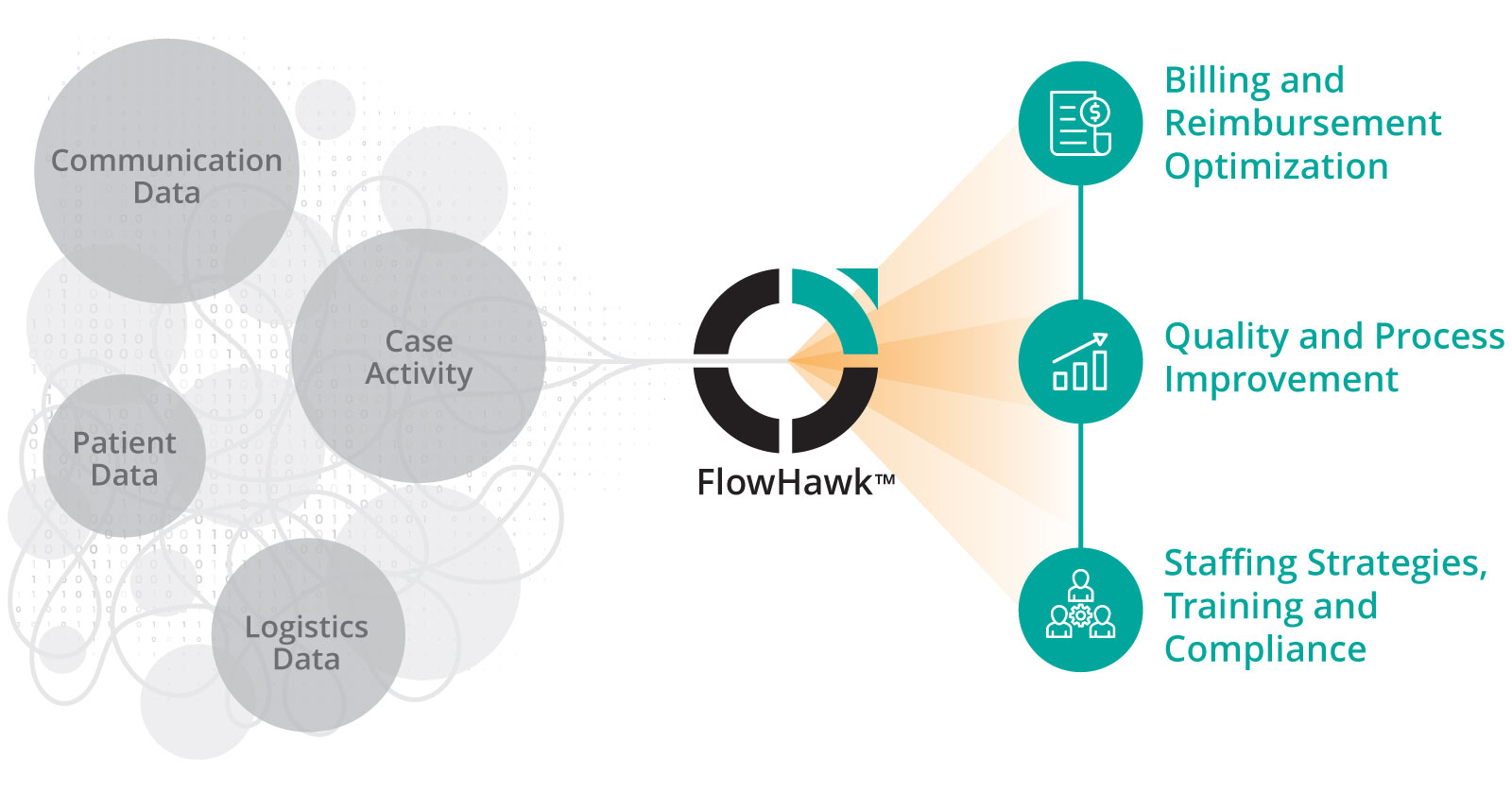
FlowHawk™ is built to streamline clinical workflows for organ transplantation with the ability to scale across your enterprise for purposeful collaboration in a variety of complex care environments.
FlowHawk
Transform the organ transplant journey with more efficient workflows
What else can your data do for you?
Leverage digital tools to standardize processes and empower care teams with access to data and insights that help improve productivity, mitigate the impact of staffing shortages, and optimize billing.
“Using OmniLife Health has been great. Being involved in the conversation cuts down on repeated calls, texts, and mistakes. It is AMAZING!”
Nicole Patterson, RN, BSN, CCTC
Transplant Nurse Manager
Simplify complex workflows, don’t reinvent them
Complex care, like organ transplantation, requires a high degree of multi-disciplinary interaction. This makes it hard for hospitals and health systems to create tools or standardized workflows that work for their transplant departments.
As a result, transplant tends to get left behind, requiring teams to “make it work” by relying on email, text messages, faxes, paper-based checklists, and other forms of manual documentation or data entry.
Just “making it work” is hard work
Our HIPAA-compliant organ transplant workflow app can help your organization:
- Mitigate the risk of HIPAA violations and security breaches
- Improve productivity to alleviate staffing shortages
- Reduce burnout by improving staff experience
- Analyze time data to enhance operations, staff training and monitoring, billing optimization, and business and clinical outcomes
Enterprise SaaS platform
- Scalable to grow with your organization
- Expandable into other complex clinical environments
- Centralized, single source of truth
Workflow automation
- Integrates with existing processes
- Digitizes paper-based checklists
- Closed-loop communications
Purpose-built
- Designed for organ transplant
- Customizable
HIPAA-compliant SMS/email communications
- Meet security requirements
- Maintain compliance in mobile
- ONC Certified
- HITRUST Certified
EHR augmentation
- Ability to bring semantic data directly into the EHR
- Avoids manual documentation
API
- Connects with external systems such as logistics and pumps
- Makes data from external systems actionable/useful at point of care
Data services & reporting
- Staffing Optimization: Staff monitoring and activity tracking
- Billing Optimization: Time study reports
- Operational Optimization: Quality and process improvement
- Communication logs
Reimbursement
- Allowable cost on the cost report as a pre-transplant expense
Revenue Capture
- Optimize time study accuracy and compliance with OmniLife data
- Optimize procurement surgery billing
Integrations
FlowHawk integrates with all the critical systems you rely on for organ transplantation and care coordination. Also ask us about custom integrations.
85+ EHRs Supported
Logistics Software
Clinical Decision Support Tools
Provider Networks

Mailing Address
9450 SW Gemini Dr., PMB 69936
Beaverton, OR 97008-7105